Email Spoofing: The Internet is part of one’s everyday life and makes a huge impact on their personal data. People are spending most of their time on mobile screens, socialising with people, learning about different cultures and their practices.
In this all, people left a lot of personal data that can be attacked and used by hackers. Hackers are always looking for ways to exploit vulnerabilities in computer systems and networks, and there are several methods they use to achieve their goals.

Here in this article, we are going to discuss some common hacking techniques, including email spoofing, port scanning, SQL injection, and IP tracing, and will also know some of the most used hacking practices. So that, you can be aware of the possible ways in which you can be robbed over the internet, and can avoid those things.
Also Read
What Email Spoofing is?
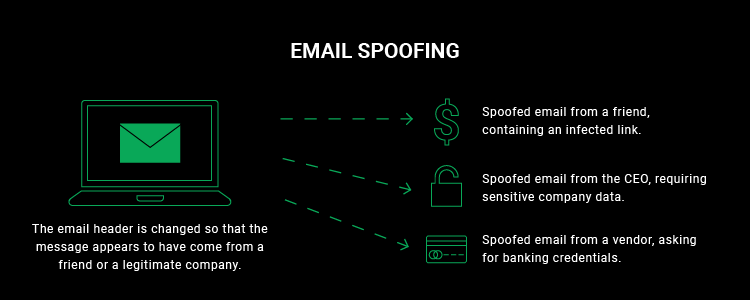
Email spoofing is a method of collecting someone’s personal data through the help of an email. This is a technique used by hackers to send emails that appear to be from a legitimate source, such as a bank or a company.
By doing so they get the trust of the audience to fill out the information they need, and to attack their credentials with ease. This method is among the most dangerous as well as often used.
To protect yourself from such emails, it is very important to be cautious while opening an email. You must know who the sender is, and must not click on any link that you feel doubtful about.
You can also use some of the best email authentication tools like SPF, DKIM, and DMARC to access the reliability and authenticity of any email whatsoever.
What is Port Scanning?
One of the most developed ways of getting into one’s computer is the method of port scanning. Ports are the connecting lines between different applications of one’s desktop, and hackers can use port scanning to find the vulnerabilities in one’s computer and get access to it.
A single vulnerable port in your computer can be the reason for the devastation and leakings of your personal data to a hacker, which he can use for any malicious activity.
To protect yourself from port scanning one must keep his computer up-to-date with the latest security patches and updates. Additionally, you can use firewalls and intrusion detection systems to monitor network traffic and identify any unusual activity.
What SQL Injection and How To Prevent It?
Another method to hack someone’s personal data is by using the vulnerabilities in web applications that use SQL databases. Most users get access to SQL databases to store their data, which in this case can be problematic as the hackers can use SQL injections to get access to those data including login details, and other financial data.
SQL injection attacks work by inserting malicious SQL statements into web application inputs, such as search boxes or login forms, to bypass security measures and gain access to the underlying database.

To protect yourselves from such practices, one must use secure coding practices when developing applications. In this way, they will be more safeguarded and protected from the evil hackers of society.
Also Read
Email Marketing: Why it’s Important in 2023, and What are the New Features?
What is IP Tracing?
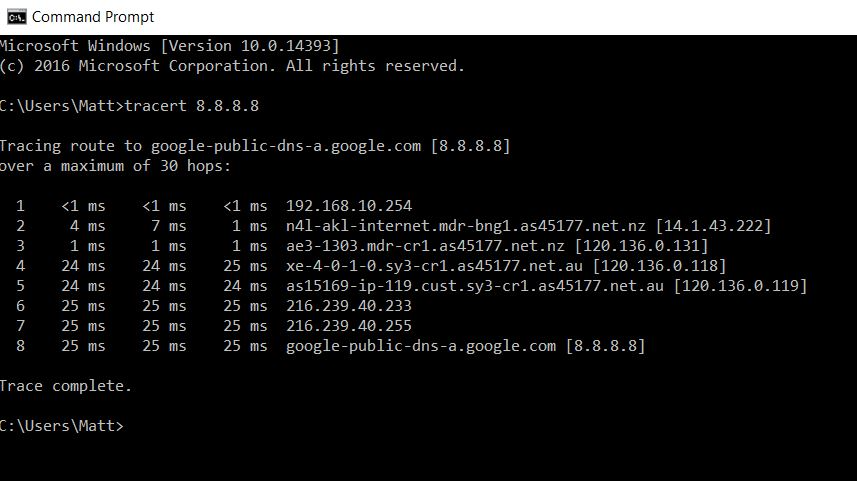
The last topic of our today’s list is the technique used to determine the location of a computer over the Internet. Every other computer on a network has a unique IP address, which can be used to determine the physical location of a computer by hackers.
IP tracing is one of the most basic and effective ways of getting one’s location in this era. Hackers use these IP addresses to launch attacks on the computer and to get the information they need.
To protect yourselves from IP tracing one must use a Virtual Private Network while connecting to the internet. In this way, the IP address of a computer gets masked up by the VPN. It makes your visit to the internet an easy one.
You can also use anti-malware systems to protect your computers from such malicious activities.
Most Used Hacking Practices By Hackers in 2023
There are a number of hacking practices that have played a great role in 2022 and are still continuing to be
in real trouble. Some of those practices include-

- Phishing
Phishing is the technique used to get the personal information of a user through any means possible. Including emails, messages, and calls. This has been one of the major ways to rob people in the past. It is continuing with a large number of hackers in it.
- Social Engineering
Social engineering is a technique used by hackers to manipulate users into divulging personal information. Social engineering attacks can take many forms, including phone calls, emails, or even in-person interactions. The goal of social engineering is to gain the victim’s trust and convince them to provide sensitive information.
- Malware
Malware is a technique in which a hacker implants software in the user’s computer. That software helps him get the information he needs. Malware can take many forms, including viruses, trojans, and spyware. Once installed, malware can monitor the victim’s activities, steal login credentials, and even take control of their computer.
Also Read
Conclusion
There are a number of ways in which hackers are getting access to the personal information of users all around the world. Whether it’s using SQL injection, port scanning, and email spoofing, hackers are being prone to making their attacks possible on the user’s computers.
To tackle these attacks, and to keep our identity safe and intact. We must also follow the very best practices to safeguard our credentials and personal information over the internet. We must follow the guidelines mentioned in this article, and keep our systems up-to-date.
About Our Company
We the times4server are one of the best emerging agencies for email marketing and digital marketing services worldwide. We believe in the concept of evolving industrialization with the induction of technology in it.
Time4servers has worked with hundreds of businesses in establishing their brand awareness and availing them of the potential market over the Internet.
We are all set to work for a better tomorrow. The only question is, are you?
Frequently Asked Questions
Social engineering is a technique used by hackers to manipulate users into divulging personal information.
One can protect himself from phishing activities by avoiding clicking on suspicious links or downloading attachments. Always check the URL of the website you are visiting and be wary of sites that ask for personal information.
The best way in which a computer can be protected from malware is by keeping your operating system and software up-to-date with the latest security patches and updates.
In this case, you should immediately stop using the affected website or application and report the incident to the website’s owner or administrator. You should also change your passwords and monitor your accounts for any suspicious activity.
